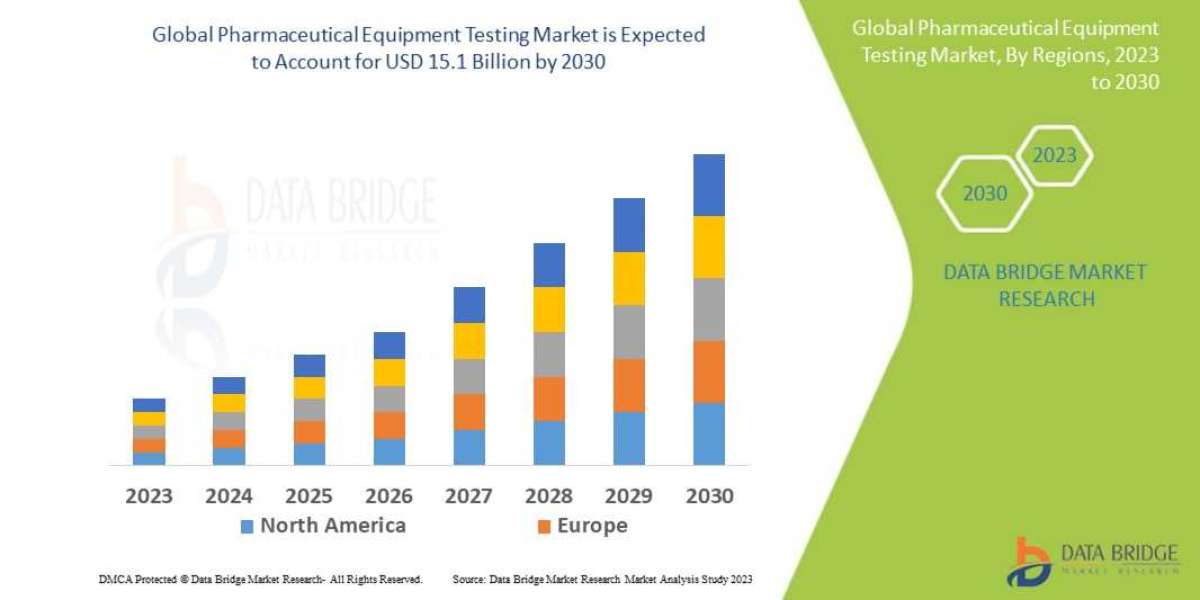
In today's digitally connected world, the security of your applications and data is of paramount importance. As businesses increasingly rely on cloud platforms like Heroku to power their applications, ensuring the safety and security of these platforms is a top priority. This comprehensive guide explores the best practices for Heroku security, covering key aspects to keep your apps safe and secure.
In this article we will discuss Best Salesforce Heroku Integration Services in India.
Understanding Heroku Security
Heroku, a cloud platform-as-a-service (PaaS) provider, offers a wide array of features and tools to help developers deploy and manage applications seamlessly. However, the responsibility for security is shared between Heroku and the application owners. Let's delve into the best practices that can help you maintain robust security on the Heroku platform.
- Authentication and Access Control
- Multi-Factor Authentication (MFA): Enable MFA for your Heroku account. This adds an extra layer of security by requiring users to provide two or more authentication factors before gaining access.
- Access Control: Implement the principle of least privilege. Only grant access to those who require it to perform their duties. Utilize Heroku's access control features to manage permissions effectively.
- Data Encryption
- SSL/TLS Encryption: Use SSL/TLS encryption for data in transit. Heroku provides built-in support for adding SSL certificates to your applications.
- Data at Rest Encryption: Encrypt sensitive data stored in your Heroku Postgres databases using industry-standard encryption mechanisms.
- Application Security
- Regular Updates: Keep your application's software and dependencies up to date. Vulnerabilities in outdated software can be exploited by attackers.
- Penetration Testing: Conduct regular penetration testing to identify and address vulnerabilities in your applications.
- Web Application Firewall (WAF): Implement a WAF to protect against common web application attacks like SQL injection and cross-site scripting (XSS).
- Monitoring and Logging
- Real-Time Monitoring: Set up real-time monitoring to detect and respond to security incidents promptly.
- Logging: Enable detailed logging to capture information about access, errors, and security events. Review logs regularly for unusual activities.
- Container Security
- Containerization: If using containers, ensure container security best practices are followed, such as regularly scanning container images for vulnerabilities.
- Compliance and Governance
- Compliance Standards: Depending on your industry, adhere to relevant compliance standards like GDPR, HIPAA, or PCI DSS.
- Audit Trails: Maintain audit trails and documentation to demonstrate compliance efforts.
- Incident Response
- Incident Response Plan: Develop a comprehensive incident response plan that outlines how to handle security incidents, including reporting and recovery procedures.
- Security Testing: Test your incident response plan through simulations or tabletop exercises to ensure its effectiveness.
- Data Backups
- Regular Backups: Schedule regular backups of your application data and configurations. Verify the integrity of backups to ensure recoverability.
- Employee Training
- Security Training: Train your employees on security best practices. Human error is a common source of security breaches.
- Third-Party Integrations
- Evaluate Third Parties: If you integrate third-party services or plugins, assess their security practices and ensure they align with your security requirements.
- Continuous Improvement
- Security Audits: Conduct regular security audits to identify vulnerabilities and areas for improvement.
- Stay Informed: Stay informed about security threats and updates related to Heroku and your application's dependencies.
Conclusion
Security is an ongoing process, and safeguarding your applications on Heroku requires continuous effort. However, to fully harness the potential of Heroku Enterprise, partnering with the best Salesforce implementation company in India and utilizing Salesforce consultants is essential.
By following these best practices, you can significantly enhance the security posture of your Heroku-hosted applications. Remember that security is a shared responsibility between you and the cloud provider, so stay vigilant, keep systems up to date, and adapt to emerging threats. With a proactive approach, you can enjoy the benefits of Heroku while keeping your applications safe and secure.This article explores the tailored solutions offered by Heroku Enterprise, emphasizing how partnering with the best Salesforce implementation company in India can maximize its benefits.
Heroku's robust security features, when combined with these best practices, create a strong defense against modern cyber threats. So, whether you're a developer, an IT administrator, or a business owner, prioritize Heroku security to protect your digital assets and maintain the trust of your users.In this article we will discuss Best Salesforce Heroku Integration Services in India.